Cloud
Databricks
How AI is Rebuilding Cybersecurity With Databricks Data Intelligence
December 19, 2025
Article

CK Editorial Team
6
min read
Security leaders are facing a structural shift in how threats operate and how defences must respond. Attack surfaces keep expanding, adversaries are using automation and AI to accelerate every stage of the kill chain, and organizations are overwhelmed by fragmented telemetry that raises cost without improving clarity.
All of this points to a shift:
Cybersecurity is becoming a data and AI problem.
Resilience now depends on how well teams unify their data, create context at scale and apply AI safely across operations. Organizations that make this shift gain earlier detection, faster response and a more intentional, intelligence-driven SOC.
Why SOC teams feel stuck
When you talk with SOC leaders, the same themes repeat:
Data silos
Security, SaaS and business telemetry sit in disconnected systems, leaving analysts to manually piece together what should already be correlated.Rising SIEM costs
Traditional ingestion models force teams to trade visibility for affordability as data volumes grow faster than budgets.Low-fidelity alerting
SOCs face constant noise from uncontextualized alerts, making it hard to focus on issues that genuinely matter to the business.Vendor sprawl
Dozens of overlapping tools create inconsistent schemas and workflows, fragmenting visibility and slowing coordinated action.AI not production-ready
Most environments lack the unified data and scalable architecture needed to operationalize AI beyond isolated pilots.
Security as a Data Intelligence Problem
Security teams aren’t limited by tools but by the lack of a shared intelligence layer. When security, IT and business data sit in one governed foundation, the SOC gains the context fragmented systems can’t provide.
From that kind of foundation, four outcomes become possible:
Unified security data for full spectrum visibility
Self-service security insights so any analyst can ask and answer questions in real time
Efficient SecOps at scale with AI agents doing the heavy lifting
A modern, open SOC architecture that integrates rather than replaces
With unified data, AI and automation shift the SOC from reactive alerts to intelligence-driven operations.
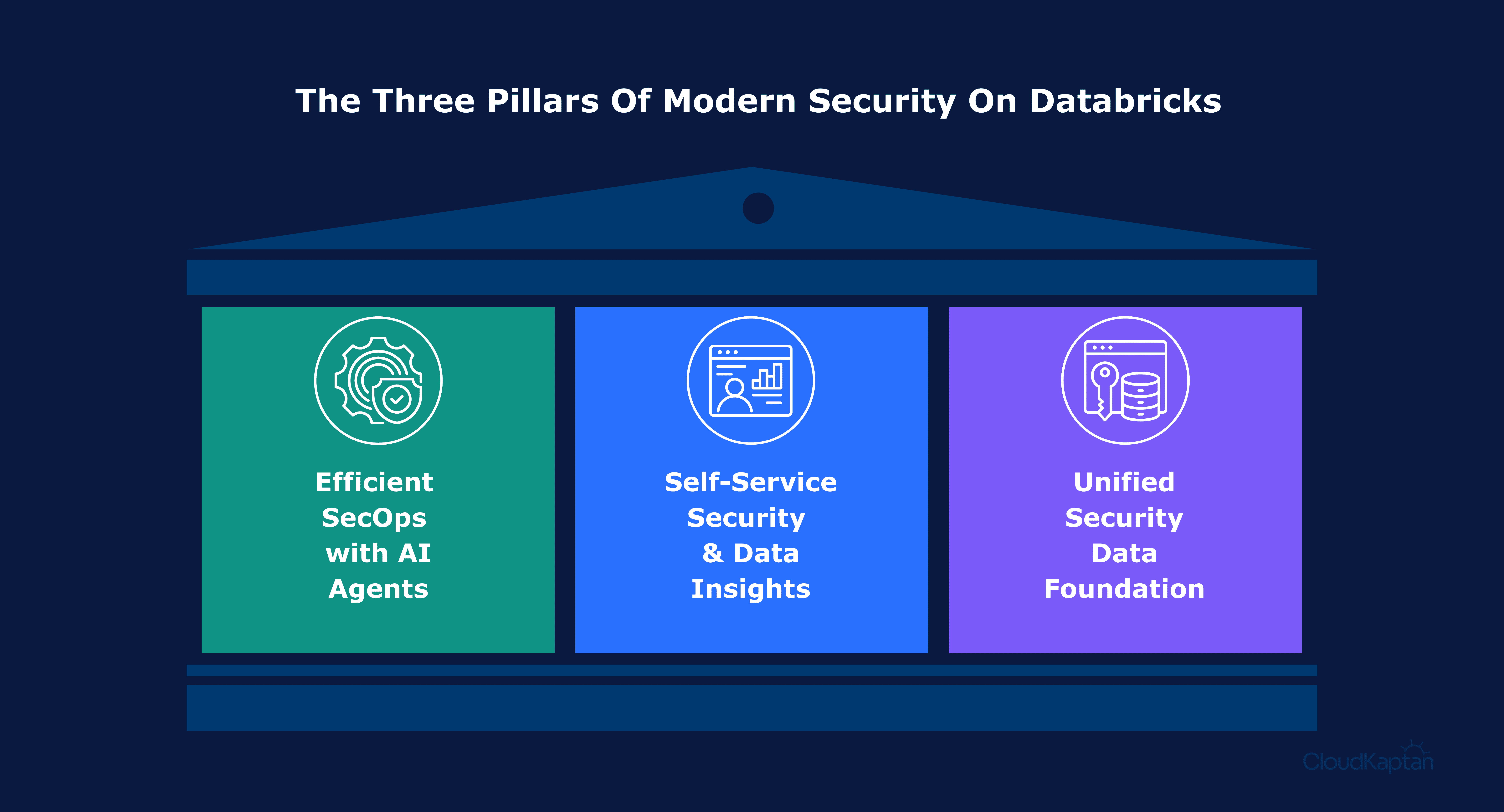
The Three Pillars of Modern Security on Databricks
Databricks organizes its cybersecurity vision around three pillars that map nicely to real-world needs.
More efficient SecOps with Agent Bricks
Modern threats operate at machine speed , so defenders need automation that goes beyond routing tickets.
Agent Bricks provides security teams production ready AI agents on the security lakehouse. These agents can:
Triage alerts using context from across your environment
Enrich incidents automatically with data from SIEM, EDR, SOAR and other sources
Summarize investigation findings consistently
Trigger orchestrated responses through existing tools
Because the agents run on governed data with Unity Catalog and the Databricks AI Security Framework, security teams retain control over model behaviour, access and audited.
The intent is not to replace analysts but to remove the repetitive work like basic enrichment and first pass triage.
Self-service security and data insights
A recurring bottleneck in large organizations is the dependence on central data teams. Security practitioners wait for data engineering support to answer basic questions like:
“How often has this IP talked to that asset in the past 30 days?”
“Show me failed logins for this user across all SaaS systems.”
Databricks tackles this with Databricks One and AI/BI Genie, which empowers users with governed security data in interfaces that work for different skill levels:
Analysts can use SQL, Python, visual tools or natural language queries.
Security leaders can explore dashboards that tie security posture to business impact.
Business stakeholders can safely consume security insights without needing a security data dictionary.
When governed security data is organized into usable domains, analysts can investigate test hypotheses instantly rather than relying on reporting cycles. This leads to faster investigations, less back and forth and fewer missed signals.
A unified security data foundation
The third pillar is the one everything else depends on.
Most SOCs today operate across multiple clouds, SaaS applications and on-prem infrastructure. Logs are stored in different formats and schemas making it difficult to form a consistent view of activity.
Databricks proposes turning your enterprise lakehouse into a security lakehouse :
Use Lakebase, for low-latency transactional data.
Land all security and IT telemetry in open formats like Delta Lake with schemas such as OCSF.
Govern it with Unity Catalog for controlled access , lineage and auditability.
A single governed data foundation lets all detection and response tool operate from the same source of truth, improving SOC consistency. With that in place, building new detections or analytics becomes logical.
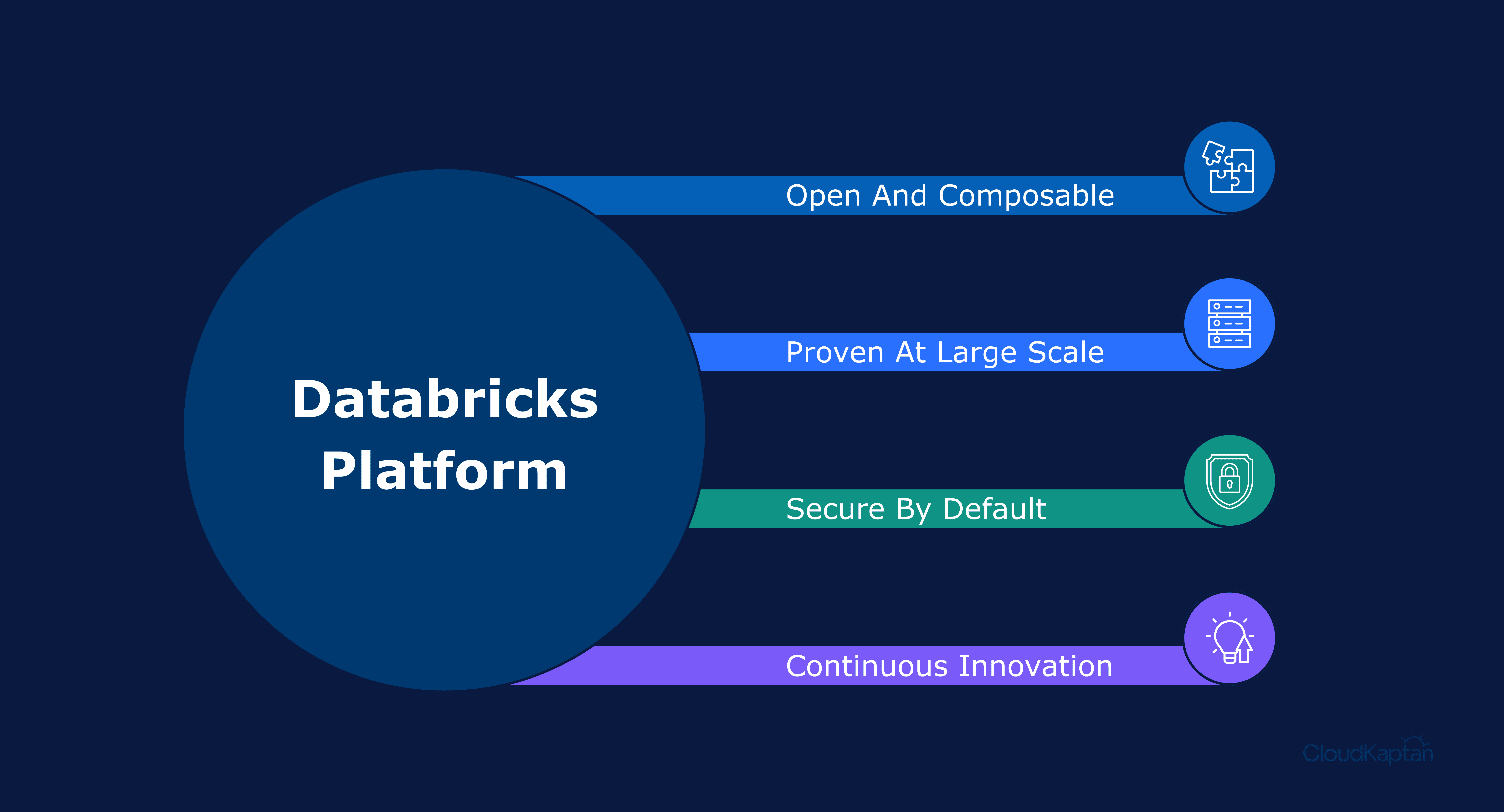
What makes the Databricks approach different
The Databricks approach is more focused on giving you a platform that your existing stack can plug into.
A few aspects stand out:
Open and composable
Databricks can serve as an analytics engine, a parallel detection layer or the SOC backbone, using open formats that integrate with existing SIEM and SOAR tools without requiring a rip-and-replace.Proven at large scale
The platform supports organizations like Abnormal AI, Rivian, Akamai, Palo Alto Networks, Arctic Wolf and SAP ECS, handling trillions of events, petabytes of data and strict uptime needs.Secure by default
Fine grained access control, multicloud deployment and integrated AI risk management ensure the platform doesn’t become a blind spot.Continuous innovation
The platform evolves with new standards, AI techniques and governance updates to keep pace with attacker behavior and regulatory expectations.
For security leaders, this combination of openness, scale and governance enables modernization at your own pace, while keeping ownership of data and detection content.
How to move toward this model
Most security programs can take these pragmatic steps to get started:
Unify one data domain
such as identity logs, EDR telemetry or cloud audit logs—and prove out better investigations before expanding.Offload a expensive workload
Move historical analytics or long term threat hunting queries off your SIEM and onto Databricks. Use this to relieve cost pressure while increasing flexibility.Pilot an AI agent in a narrow workflow
Start with alert enrichment or case summarization, and expand based on trust and results.Bring business context closer to detections
Connect asset inventories, HR data and critical application metadata so that high value users and systems are automatically prioritized in scoring and triage.Use open standards for any new integration
When ingesting a new log source or deploying a new security tool, Favor OCSF or other open schemas. This keeps your options open and makes downstream analytics simpler.
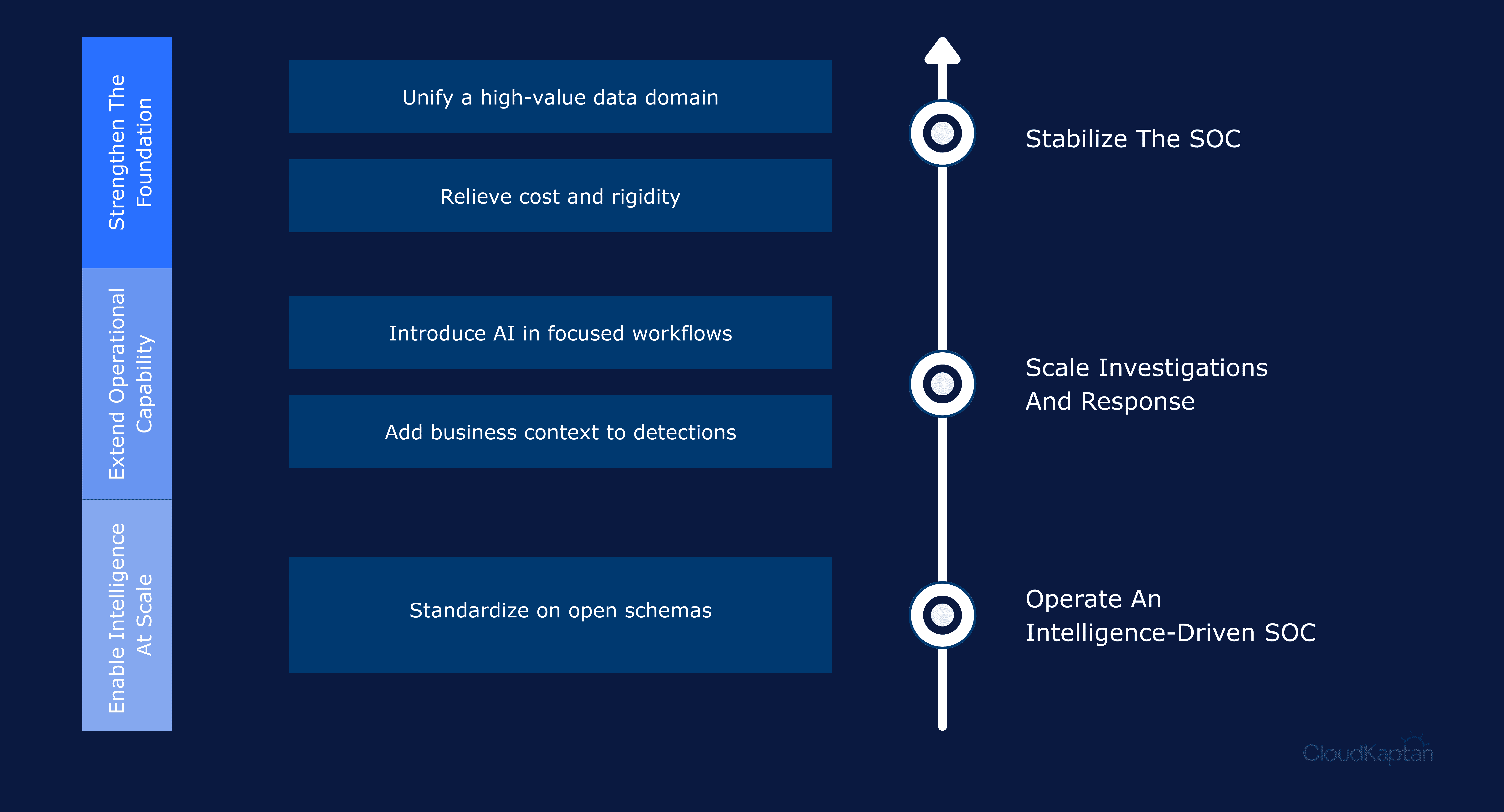
Over time, these steps add up to a SOC that is less constrained by tool boundaries and more defined by what your team can build on top of a unified security Lakehouse.
The Shift Toward Data-Driven Defence
Strong cyber defence comes from a unified data foundation, not from accumulating more tools. When security teams ground their operations in shared data and governed AI, they regain leverage over complexity.
Unify the signals. Govern them carefully. Put AI agents and self-service analytics in the hands of your security experts. Integrate with the tools that already work for you, instead of starting from scratch.
That is what allows security leaders to get out of permanent firefighting mode and start shaping the future of their own SOC.

